SSH学习笔记
# SSH 简介
SSH(Secure Shell)是一种能够以安全方式提供远程登录的协议,也是目前远程管理Linux系统的首选方式。
OpenSSH (opens new window) 是 SSH 协议的免费开源实现。
OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It encrypts all traffic to eliminate eavesdropping, connection hijacking, and other attacks. In addition, OpenSSH provides a large suite of secure tunneling capabilities, several authentication methods, and sophisticated configuration options.
The OpenSSH suite consists of the following tools:
- Remote operations are done using ssh (opens new window), scp (opens new window), and sftp (opens new window).
- Key management with ssh-add (opens new window), ssh-keysign (opens new window), ssh-keyscan (opens new window), and ssh-keygen (opens new window).
- The service side consists of sshd (opens new window), sftp-server (opens new window), and ssh-agent (opens new window).
# SSH 环境搭建
查看系统是否已经安装OpenSSH:
# 检查系统上是否存在sshd进程
ps aux | grep sshd
# 检查系统是否安装了OpenSSH客户端,如果SSH客户端已安装并正确配置,它将显示路径:/usr/bin/ssh
which ssh
# 检查系统是否安装了OpenSSH
rpm -qa | grep openssh
# 检查系统是否安装了OpenSSH服务端
rpm -qa | grep openssh-server
# 检查系统是否安装了OpenSSH客户端
rpm -qa | grep openssh-clients
# 查看版本
ssh -V
2
3
4
5
6
7
8
9
10
11
12
13
14
15
如果在一台Linux主机上通过ssh命令登录另一台主机,需要安装SSH的客户端,这在最小化系统中并不默认安装,所以需要手动更新安装。
yum install openssh-clients -y
被登录的主机,需要安装SSH的服务端,可以按照以下步骤进行操作:
安装OpenSSH软件包(通常在Linux系统中已经默认安装)。
yum install openssh-server -y1打开SSH服务的配置文件,该文件位于/etc/ssh/sshd_config目录下,名为"sshd_config"。sshd_config 是 SSH 守护程序(sshd)的配置文件,用于定义 SSH 服务器的行为。
# 从根目录开始递归搜索所有目录,查找名为 sshd_config 的文件 find / -name sshd_config1
2使用编辑器(比如vi或nano)打开sshd_config文件并修改相关设置。
常见的配置选项:
# 指定SSH连接所使用的端口号,默认为22 Port 22 # 允许root用户登录 PermitRootLogin yes # 启用密码认证 PasswordAuthentication yes # 启用公钥认证 PubkeyAuthentication yes # 公钥认证文件 AuthorizedKeysFile .ssh/authorized_keys # 启用RSA认证 RSAAuthentication yes # Match配置: # https://www.cnblogs.com/joshua317/p/14148694.html # https://segmentfault.com/a/11900000148224001
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20保存并关闭sshd_config文件。
重新启动SSH服务。
# 查看SSH服务运行状态 systemctl status sshd.service # 启动SSH服务 systemctl start sshd.service # 停止SSH服务 systemctl stop sshd.service # 重启SSH服务 systemctl restart sshd.service1
2
3
4
5
6
7
8
# 远程登录命令
远程登录命令格式:
ssh 用户名@主机地址
远程登录可以使用密码登录和无密码登录(公钥登录)。
# 使用密码登录
使用密码登录远程主机:
[root@localhost0132 ~]# ssh root@192.168.1.31
The authenticity of host '192.168.1.31 (192.168.1.31)' can't be established.
ECDSA key fingerprint is SHA256:NLUDWgWXkB6X0A2032EYKLX2kIOHTutiRnhPE8ik3Jg.
ECDSA key fingerprint is MD5:c6:72:64:93:07:2d:b5:fd:d5:2b:5e:31:c7:03:da:16.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.1.31' (ECDSA) to the list of known hosts.
root@192.168.1.31's password:
Last login: Sun Jun 23 12:43:22 2024 from 192.168.1.102
[root@localhost0131 ~]#
2
3
4
5
6
7
8
9
# 使用公钥登录
SSH 公钥登录的原理涉及到公钥和私钥的生成以及使用。SSH 公钥登录的过程如下:
用户生成一对公钥和私钥。
用户将自己的公钥添加到远程服务器的~/.ssh/authorized_keys文件中。
用户尝试通过SSH登录远程服务器时,服务器收到用户的公钥请求。
服务器检查~/.ssh/authorized_keys文件中是否有用户提供的公钥,如果有,则生成一个随机字符串,并使用用户的公钥加密。
服务器将加密的字符串发送给用户。
用户接收到加密字符串后,使用自己的私钥解密,然后将解密后的字符串发送回服务器。
服务器验证解密后的字符串与原始字符串匹配,如果匹配,则授权用户登录。
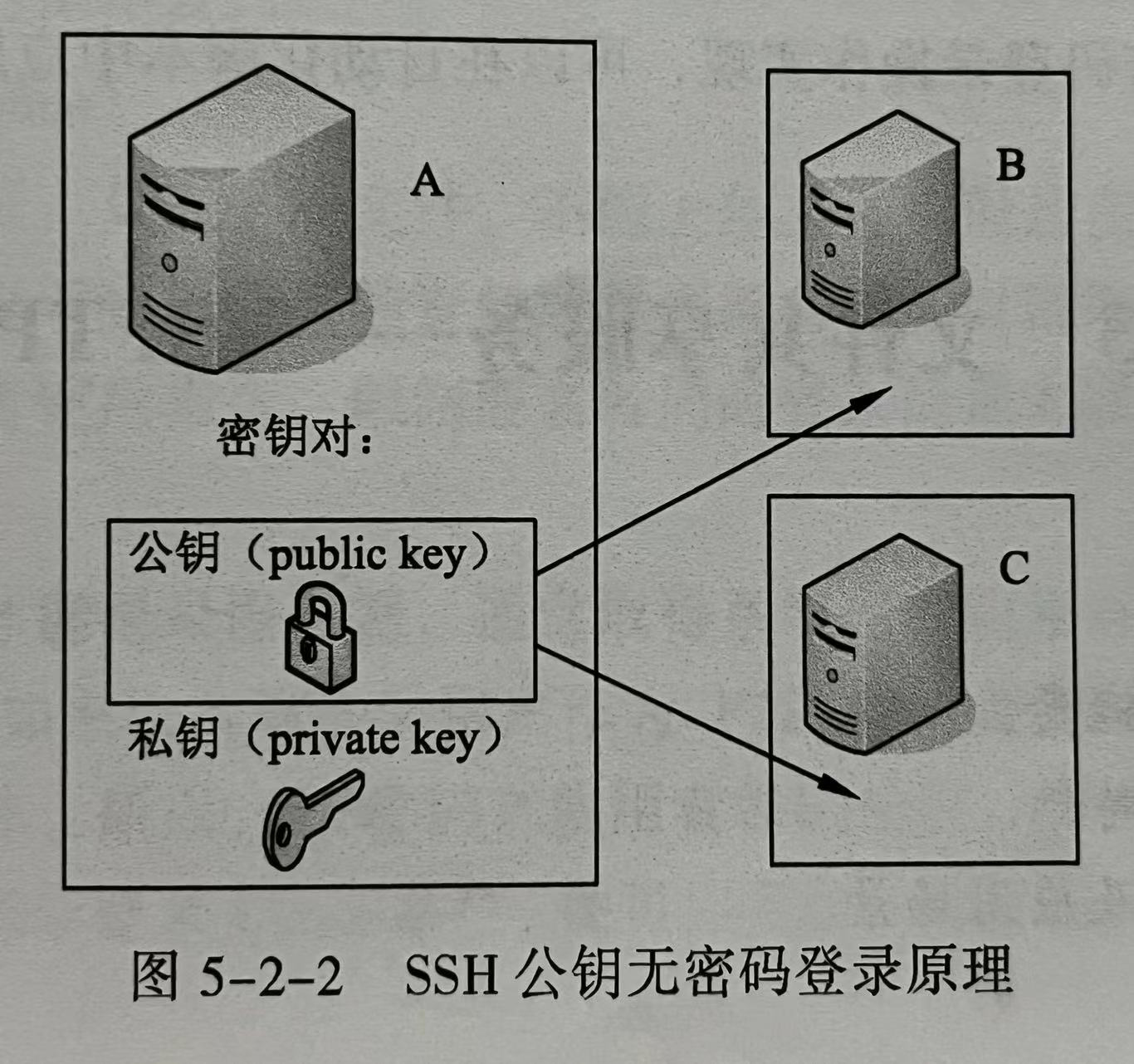
从A登录到B和C,需要在A上生成密钥对,把A的公钥复制到B和C上,就可以实现A免密登录B和C。命令主要是:
cd ~
ls -al
# 如果 ~/.ssh 不存在,创建 .ssh 并设置文件夹权限为700
mkdir .ssh
chmod 700 ~/.ssh
# 生成密钥对
ssh-keygen -t rsa -b 4096
# 将公钥上传到远程服务器。
# 原理是把当前登录用户的 ~/.ssh/id_rsa.pub 追加到要访问的远程服务器的 ~/.ssh/authorized_kes 文件中。
# ssh-copy-id user@remote_server
# 如果远程服务器的 ~/.ssh/authorized_kes 不存在,需要先创建并设置文件夹权限为600
touch authorized_keys
chmod 600 ~/.ssh/authorized_keys
# 公钥登录远程服务器
ssh user@remote_server
# 公钥登录远程服务器,-i或--identity-file 指定私钥路径
ssh -i /path/to/your/private_key user@remote_server
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# SSH 生成密钥对
ssh-keygen (opens new window) is a tool for creating new authentication key pairs for SSH. Such key pairs are used for automating logins, single sign-on, and for authenticating hosts.
The simplest way to generate a key pair is to run ssh-keygen without arguments.
First, the tool asked where to save the file. SSH keys for user authentication are usually stored in the user's .ssh directory under the home directory. However, in enterprise environments, the location is often different. The default key file name depends on the algorithm, in this case id_rsa when using the default RSA algorithm. It could also be, for example, id_dsa or id_ecdsa.
Then it asks to enter a passphrase (opens new window). The passphrase is used for encrypting the key, so that it cannot be used even if someone obtains the private key file. The passphrase should be cryptographically strong. Our online random password generator (opens new window) is one possible tool for generating strong passphrases.
SSH supports several public key algorithms for authentication keys. These include:
rsa- an old algorithm based on the difficulty of factoring large numbers. A key size of at least 2048 bits is recommended for RSA; 4096 bits is better. RSA is getting old and significant advances are being made in factoring. Choosing a different algorithm may be advisable. It is quite possible the RSA algorithm will become practically breakable in the foreseeable future. All SSH clients support this algorithm.dsa- an old US government Digital Signature Algorithm. It is based on the difficulty of computing discrete logarithms. A key size of 1024 would normally be used with it. DSA in its original form is no longer recommended.ecdsa- a new Digital Signature Algorithm standarized by the US government, using elliptic curves. This is probably a good algorithm for current applications. Only three key sizes are supported: 256, 384, and 521 (sic!) bits. We would recommend always using it with 521 bits, since the keys are still small and probably more secure than the smaller keys (even though they should be safe as well). Most SSH clients now support this algorithm.ed25519- this is a new algorithm added in OpenSSH. Support for it in clients is not yet universal. Thus its use in general purpose applications may not yet be advisable.
The algorithm is selected using the -t option and key size using the -b option. The following commands illustrate:
ssh-keygen -t rsa -b 4096
ssh-keygen -t dsa
ssh-keygen -t ecdsa -b 521
ssh-keygen -t ed25519
2
3
4
Normally, the tool prompts for the file in which to store the key. However, it can also be specified on the command line using the -f <filename> option.
ssh-keygen -f ~/tatu-key-ecdsa -t ecdsa -b 521
To use public key authentication, the public key must be copied to a server and installed in an authorized_keys (opens new window) file. This can be conveniently done using the ssh-copy-id (opens new window) tool. Like this:
ssh-copy-id -i ~/.ssh/tatu-key-ecdsa user@host
Once the public key has been configured on the server, the server will allow any connecting user that has the private key to log in. During the login process, the client proves possession of the private key by digitally signing the key exchange.
Here's a summary of commonly used options to the keygen tool:
-b “Bits” This option specifies the number of bits in the key. The regulations that govern the use case for SSH may require a specific key length to be used. In general, 2048 bits is considered to be sufficient for RSA keys.
-e “Export” This option allows reformatting of existing keys between the OpenSSH key file format and the format documented in RFC 4716 (opens new window), “SSH Public Key File Format”.
-p “Change the passphrase” This option allows changing the passphrase of a private key file with **[-P old_passphrase]** and **[-N new_passphrase]**, **[-f keyfile]**.
-t “Type” This option specifies the type of key to be created. Commonly used values are: - rsa for RSA (opens new window) keys - dsa for DSA (opens new window) keys - ecdsa for elliptic curve DSA (opens new window) keys
-i "Input" When ssh-keygen is required to access an existing key, this option designates the file.
-f "File" Specifies name of the file in which to store the created key.
-N "New" Provides a new passphrase for the key.
-P "Passphrase" Provides the (old) passphrase when reading a key.
-c "Comment" Changes the comment for a keyfile.
-p Change the passphrase of a private key file.
-q Silence ssh-keygen.
-v Verbose mode.
-l "Fingerprint" Print the fingerprint of the specified public key.
-B "Bubble babble" Shows a "bubble babble" (Tectia format) fingerprint of a keyfile.
-F Search for a specified hostname in a known_hosts file.
-R Remove all keys belonging to a hostname from a known_hosts file.
-y Read a private OpenSSH format file and print an OpenSSH public key to stdout.
This only listed the most commonly used options. For full usage, including the more exotic and special-purpose options, use the man ssh-keygen command.
# SFTP 服务器搭建
SFTP(Secure File Transfer Protocol )是一个可以为文件进行安全传输的网络协议。
SFTP和FTP的区别
- 链接方式:FTP 使用 TCP 端口21建立连接。SFTP 是在客户端和服务器之间通过SSH协议(TCP端口22)建立的安全连接来传输文件。
- 安全性:SFTP 使用加密传输认证信息和传输的数据,使用 SFTP 相对于 FTP 安全
- 效率:SFTP 使用加密解密技术,传输效率比普通的 FTP 要低得多。
# 创建SFTP用户与组
groupadd javgrp
usermod -G javgrp root
useradd -G javgrp -m -d /home/javadm -s /bin/bash javadm
useradd -G javgrp -m -d /home/appadm -s /bin/bash appadm
mkdir -p /appl/sftp-staging/jd/inbound
chown -R javadm:javgrp /appl/sftp-staging
chmod 750 /appl/sftp-staging
chmod 750 /appl/sftp-staging/jd
chmod 770 /appl/sftp-staging/jd/inbound
ln -s /appl/sftp-staging/jd /home/appadm/jd
mkdir -p /home/appadm/.ssh
chown appadm:javgrp /home/appadm/.ssh
chmod 750 /home/appadm/.ssh
touch /home/appadm/.ssh/authorized_keys
chown appadm:javgrp /home/appadm/.ssh/authorized_keys
chmod 750 /home/appadm/.ssh/authorized_keys
vim /home/appadm/.ssh/authorized_keys
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# 配置sshd_config
vim /etc/ssh/sshd_config
#Subsystem sftp /usr/libexec/openssh/sftp-server
#Subsystem sftp /usr/lib/openssh/sftp-server
#Subsystem sftp internal-sft # 指定使用sftp服务使用系统自带的internal-sftp
#Match Group sftpgroup # 匹配sftp组的用户,若要匹配多个组,可用逗号分开
#X11Forwarding no # 禁止用户使用端口转发
#AllowTcpForwarding no # 禁止用户使用端口转发
#ChrootDirectory /home/sftp/%u # 限制用户的根目录
#ForceCommand internal-sftp # 只能用于sftp登录
2
3
4
5
6
7
8
sftp-server和internal-sftp都是OpenSSH的一部分。
sftp-server是一个独立的二进制文件。
internal-sftp是一个配置关键字,无需外部二进制文件额外启动一个进程,整合在sshd进程内了。
internal-sftp相较于 /usr/lib/openssh/sftp-server 优点在于:
- 性能好,无需额外进程;
- 安全性好,无需用户登录shell,且可使用ChrootDirectory 限制sftp行为活动的目录;
- sftp-server 的存在主要是向后兼容。
# 连通性测试
sftp -oPort=22 sftpusr@192.168.1.31
put /opt/foo.txt /home/sftpusr/sftp-staging/tms/inbound
2
